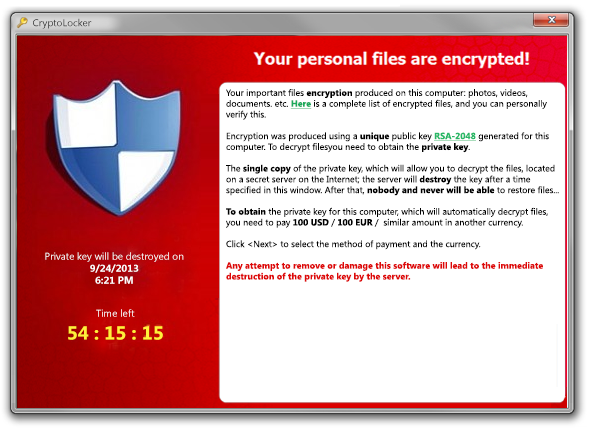
Cyber security packages by us are aligned with all cyber security framework requirements. This includes identifying threats, network protection, intrusion detection, incident response, and business recovery after a cyber attack.
Identifying Threats
In our process for finding threats, we look at IT flaws and decide if they could be used to break into your system. It’s a crucial component of your company’s risk management strategy. Identifying dangers enables your company to take preventative measures.
Network Protection
Our network protection improves the capacity to reduce the attack surface tremendously. It assists in preventing employees from using applications to visit risky domains. Internet domains that host phishing scams, exploits, and other malicious information are deemed risky.
Intrusion Detection
Our monitoring system called an intrusion detection system (IDS) looks for abnormal activity and sends out alarms when it does. A security operations centre (SOC) analyst or incident responder can analyse the problem and take the necessary steps to eliminate the threat based on these notifications.
Incident Response
We will provide an Incident response plan which has a systematic method of dealing with and managing the fallout from a security breach or cyberattack. The objective is to approach the situation in a way that minimises harm, cuts down on recovery time, and lowers expenses.
Business Recovery
This is the process of developing preventive and recovery measures to handle possible cyber threats to your organization or guarantee process continuity after a cyberattack. This plan has three key elements: resilience, recovery, and contingency. An organization can increase resilience by designing critical functions and infrastructures with various disaster possibilities in mind; this can include staffing rotations, data redundancy, and maintaining a surplus of capacity.
| Cyber Security Services Available |
| Asset Management Business Environment Governance Risk Assessment Risk Management Strategy Supply Chain Management |
| Access Management Awareness and Training Data Security Information Protection Processes and Procedures System Maintenance Protective Technology |
| Cybercrime Investigation Security Continuous Monitoring Detection Processes |
| Cyber Security Incident Response |
| IR Recovery Services Improvement Recovery Communication Services |